Posted by Murad Kablan ● Jan 21, 2020 9:27:55 AM
Encryption Everywhere
As the march towards digital transformation continues, the amount of digital data we need to protect continues to increase at an incredible pace. According to Visual Capitalist, about 188 million emails are sent every minute and that number will only continue to rise. Bad actors have more to gain than ever and CISOs are waging war with these cybercriminals using a constantly evolving set of security tools. Yet, despite increased spending on cybersecurity, multiple major data breaches still happen every single day.
One common technique that organizations use to protect sensitive data is by creating cybersecurity ‘safe’ zones. This practice is used to apply layers of successive security controls that create network zones with varying levels of access protections. This design allows CISOs to apply rigid controls around their most sensitive data; however, it fails to address the risks of internal attacks. In fact, according to a recent study by Mimecast, 41% of organizations have seen increases in internally sourced threats and data leaks.
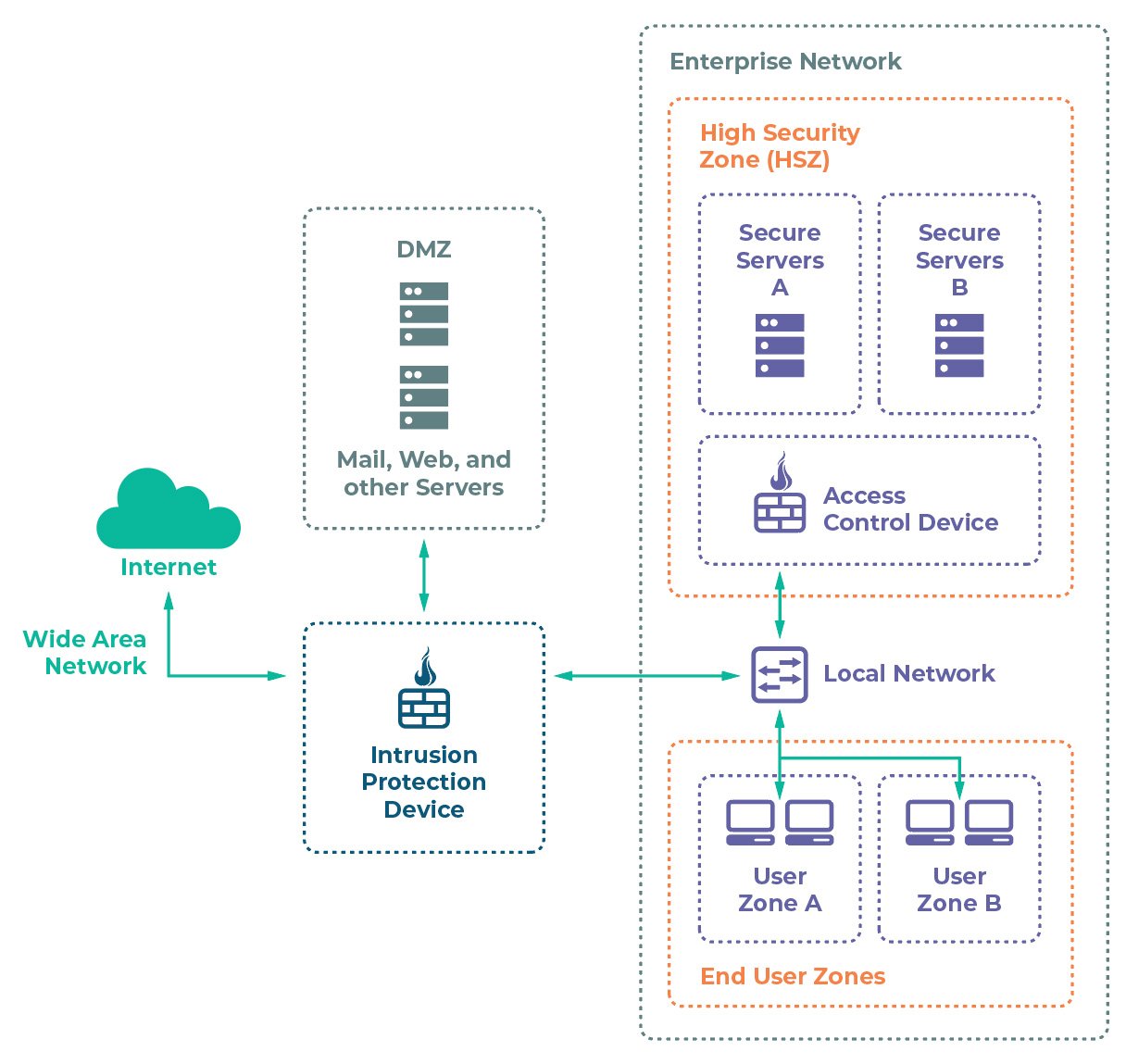
Zero Trust and the Need for Encryption
In recent years there is a new security philosophy emerging known as Zero Trust. This model doesn’t replace the use of security zones, but rather it approaches the securing of data through a new paradigm. In a Zero Trust model, CISOs assume that the bad actors will always be able to access their network infrastructure. Assuming zero-trust, what controls can CISOs use to protect their sensitive data?
The answer is a technique that has been used to secure sensitive data for centuries: encryption.
We already use encryption in our everyday lives. Most websites now use Hypertext Transfer Protocol Secure (https) to transfer data. Today about 70% of the data transferred via web browsers is encrypted via https. But encryption isn’t broadly used to secure internal data. Why? Encryption is expensive and complicated.
To protect data with encryption, CISOs need to encrypt both data at rest and data in motion. Data ‘at rest’ is data in storage and is easier to encrypt. Disk drives with hardware-based encryption are inexpensive and readily available. On the other hand, encryption of moving data, or data in transit on a network requires specialized and expensive equipment.
The reason that network encryption hardware is so expensive is that encrypting large volumes of data in real-time is an extremely processor-intensive application. As the amount of data and the network speeds needed to move that data have increased, encryption hardware has needed to become more powerful to keep up. Historically, the only way to make hardware faster has been to scale it up which meant that the hardware could only go as fast as the processors and memory it was built upon. Fast hardware is expensive. As one of my cycling friends recently told me, you have to “spend fast to go fast”.
Even though CISOs budgets are growing, they haven’t had the resources to apply encryption everywhere... until now.
Scale OUT, not UP
Fundamentally, data encryption is just an application. And with the introduction of cloud computing, we now know that scaling up isn’t the only way to make applications run faster. Rather than scale-up, we can now scale-out. Scaling out allows us to go faster by distributing tasks across multiple computers and is much more efficient and inexpensive than scaling up. That said, even with the introduction of NFV, today’s networking equipment can really only scale up. Until now.
Now, there is a new way of deploying networking applications like encryption. This new method applies a technology called SD-IX (Software-Defined Interconnect). Instead of purpose-built rigid hardware, SD-IX uses a microservices-based architecture that operates networking applications like encryption, routing, filtering in a distributed system. Unlike traditional hardware or NFV systems, a microservices-based SD-IX platform treats servers as a pool of computing resources and allows encryption processes to dynamically scale-out across servers as needed. In a recent study comparing traditional systems that can encrypt a few dozen connections to an SD-IX based architecture, the SD-IX system is capable of encrypting orders of magnitude greater numbers of network data streams and do so at a fraction of the traditional systems’ cost.
Any CISO will tell you that developing a cybersecurity strategy is balancing cost versus risk. The cost of network encryption will be decreased by an order of magnitude and with the introduction of a microservices-based infrastructure. We are going to be one step closer to ‘encryption everywhere’ and one more step ahead of the bad guys.
------
(BTW - the clue is nineteen)
Topics: Use Cases, Enablement
